HOW TO INTEGRATE ISO 27001 CONTROLS INTO SOFTWARE DEVELOPMENT LIFE CYCLE (SDLC) ?
Information security
is just on a par with the procedures identified with it, yet we find numerous
associations concerned uniquely about whether security highlights exist and are
dynamic in their information systems, and not how they are created, executed,
kept up, and improved.
Thus, numerous
information systems neglect to protect-information, not in view of an absence
of security highlights, but since poor advancement, usage, upkeep, or
improvement practices have driven highlights to not work appropriately, or to
be effectively avoided, causing harm against which organizations were relying
on being protected.
This
article will display how an organized advancement process (SDLC – System or
Software Development Life Cycle), and ISO 27001 Certification security controls for
frameworks obtaining, improvement, and upkeep can together assistance increment
the security of data frameworks improvement forms, profiting data security,
however associations and those engaged with improvement forms also.
Why develop securely?
By implementing
secure practices in inside advancement forms, or by requesting that providers
execute them in their procedures, not exclusively is simply the data better
ensured, however associations can accomplish advantages like:
· Reduced re-work costs: security
practices uphold progressively thorough arranging and situation assessment,
prompting better characterized frameworks prerequisites and increasingly
reasonable arrangements.
· Reduced incident-costs: better
arranged frameworks and security controls limit the event and effect of
occurrences.
· Reduced upkeep personal time:
security practices uphold more command over the improvement and usage of
changes, so less time is expected to perform them, and less issues emerge.
· Reduced-liability: the appropriation
of secure practices is seen as a due ingenuity exertion to anticipate the
acknowledgment of dangers, which can limit punishments in legitimate
activities.
As for development teams, benefits
would be:
· Increased prerequisites control:
necessity changes must be assessed and formalized before implementation.
· Clear verification and approval
criteria: necessities must be related with quantifiable outcomes to be
accomplished.
· Better defenses for assets: clear
outcomes to be accomplished assistance bolster requests for assets (e.g.,
capabilities, gear, situations, and so on.).
You
should take note of that the degree by which secure improvement practices might
be implemented must adjust the requirement for security of the framework and
the profitability of the procedures, or you may wind up changing a security
issue into an efficiency issue in your advancement forms. A prescribed
instrument to help locate the correct parity is the hazard appraisal table.
SDLC: System/Software Development
Life Cycle?
The acronym SDLC can be ascribed
either to system or software when considering the development life cycle(SDLC).
In a word, SDLC covers the accompanying organized procedures:
· Analysis: picking up a superior
comprehension of what is normal from the system or software
· Design: characterizing the answer for
be implemented.
· Implementation: executing the
exercises required to make the system or software and make it accessible to
clients
· Operation: the successful utilization
of the system or software
·
Maintenance: making changes to the
system or software to ensure it does not become obsolete
·
Maintenance: making changes to the the
system or software to guarantee it doesn't wind up obsolete.
·
Disposition: disposing of the system
or software
The principal contrast with respect to the expression
"Framework/Software" is that the framework advancement life cycle
contains programming, yet additionally equipment, information, individuals,
forms, methods, offices, and materials. ISO (International Organization for
Standardization) has a few guidelines covering both the framework (ISO/IEC/IEEE
15288:2015 and ISO/IEC TR 90005:2008) and programming (ISO/IEC 12207:2008 and
ISO/IEC 90003:2014) approaches.
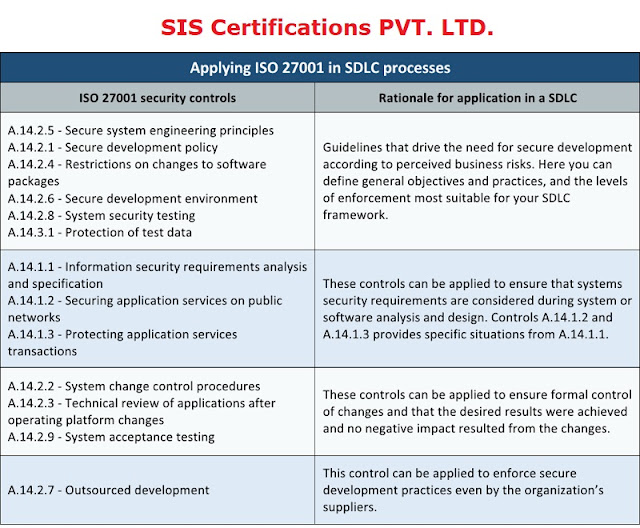
Applying ISO
27001 in the SDLC
ISO 27001 Certification has a lot of prescribed security targets and
controls, depicted in Annex A.14 and definite in ISO 27002 section 14, to guarantee
that information security is an essential piece of the frameworks life cycle,
including the improvement life cycle, while likewise covering the assurance of
information utilized for testing. By considering the accompanying controls in
SDLC forms, you can make them progressively strong, and with this, improve the
adequacy of the created information frameworks in regards to data protection:
For more information about secure system engineering
principles, see: What are secure engineering principles in ISO 27001:2013
control A.14.2.5?
The ISO 27001 Certification arrangement likewise
has a lot of measures to help security the executives ideas and help actualize
security controls indicated to ISO 27002 with respect to application security.
These are the gauges: ISO/IEC 27034-1:2011, ISO/IEC 27034-2:2015, and ISO/IEC
27034-6:2016.
Secure
processes deliver secure results
As data frameworks develop in
unpredictability and criticality, greater helplessness focuses show up, and
each of the a miscreant, or indiscreet client, needs to cause ruin on business
activities is a solitary point (e.g., an exploitable code, a handicapped
security work, a not well arranged client request, an overlooked fix, and so forth.),
and conventional improvement practices are not ready to keep up appropriate
security levels.
By adopting SDLC together with A.14
controls from ISO 27001 Certification to securely develop information systems, an association
can ensure it covers the most widely recognized dangers and, by regarding
security information a procedure, be deliberately and constantly taking a shot
at keeping up security levels and fending off its data and frameworks from
damage, while receiving the rewards of improved procedures.
Other Related Link : -
ISO Certification in Denmark
ISO Certification in United State
ISO Certification in Italy
ISO Certification in Austria
ISO Certification in Belgium
ISO Certification in Mexico
EN 14683 certification
ISO 14971 Certification
ISO 22609 Certification
ISO Certification in Denmark
ISO Certification in United State
ISO Certification in Italy
ISO Certification in Austria
ISO Certification in Belgium
ISO Certification in Mexico
EN 14683 certification
ISO 14971 Certification
ISO 22609 Certification











Thanks for this valuable information. Its very useful to me. Keep sharing.
ReplyDeleteISO 9712 certification bodies in Chennai
ISO 9712 consultants in Chennai
It's great to come across a blog like this!!! Keep posting more.
ReplyDeleteCQI AND IRCA CERTIFIED ISO 45001:2018 LEAD AUDITOR TRAINING COURSE